We attended RSAC 2024 in San Francisco from May 6-8. Our days at the conference were packed with back-to-back briefings.
Here’s some notes on our briefing with Michael Callahan (Chief Marketing Officer) of Salt Security. The briefing was organized by Jordan Steffan of ICR Lumina.
Key takeaways from the briefing:
- Salt was founded six years ago with a focus on API security.
- APIs are a big deal, given how frequently they are used by applications to share information. Michael said that some companies see 4-5 billion API calls/month – a massive number – and the challenge is to be able to detect the bad calls.
- When Salt engages with a potential customer, many say they don’t even know what APIs they have. This is partly due to loose governance around API creation, lack of documentation, rapid change cadences, and ongoing app modernization. Hence, discovery of what is represents the first port of call for many customers. Optics and visibility first, control and oversight second.
- As APIs are discovered, Salt’s toolkit analyzes APIs for similarities. One reason for this is to highlight areas for rationalization of the number and diversity of APIs, thus driving standardization and reducing the API attack surface / threat scope.
- Salt’s toolkit also continually analyzes APIs for deviation from policy, such as the absence of up-to-date documentation.
- Michael demonstrated how a developer can use ChatGPT to write an API for a system, based on declaratives around requirements, etc. Within seconds of giving the prompt, a new API was written. While powerful, Michael’s point was that generative AI used for API development will greatly expand the number of APIs in use, and thus cross-API differentiation, and thus an increased attack surface / threat scope.
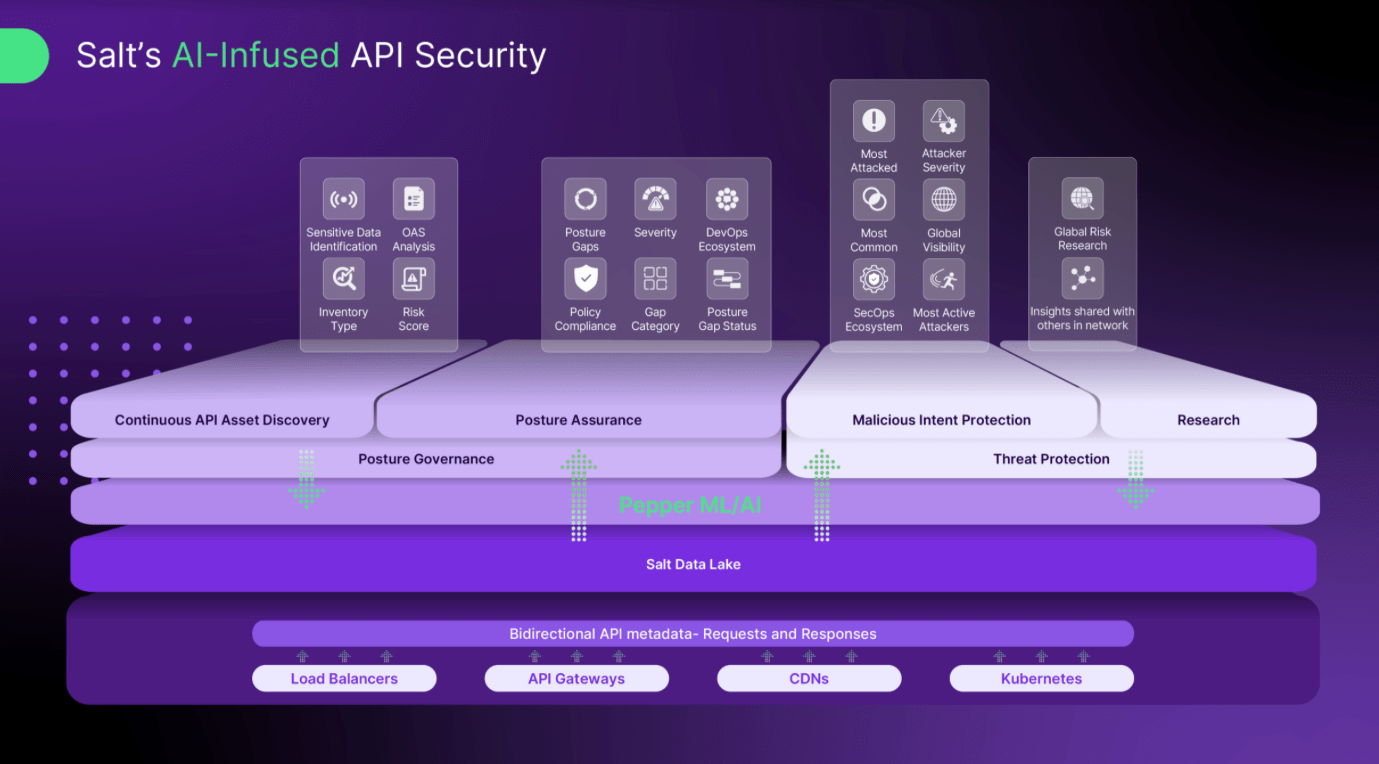
- Salt’s AI engine – called Pepper (as in, salt and pepper) – is used across the Salt platform for continuous discovery, posture analysis, and threat detection. Salt says Pepper is an “exhaustive investigator” in the discovery phase, even finding undocumenting APIs and those embedded in microservices. In the posture analysis / assurance phase, Pepper analyzes for “deviations from security best practices and highlight[s] insecure configurations.” And in the behavioral threat protection phase, Pepper looks for the abnormal, anomalous, suspicious, and potentially malicious exploits and attacks.
For more, see Salt Security.
Leave a Reply